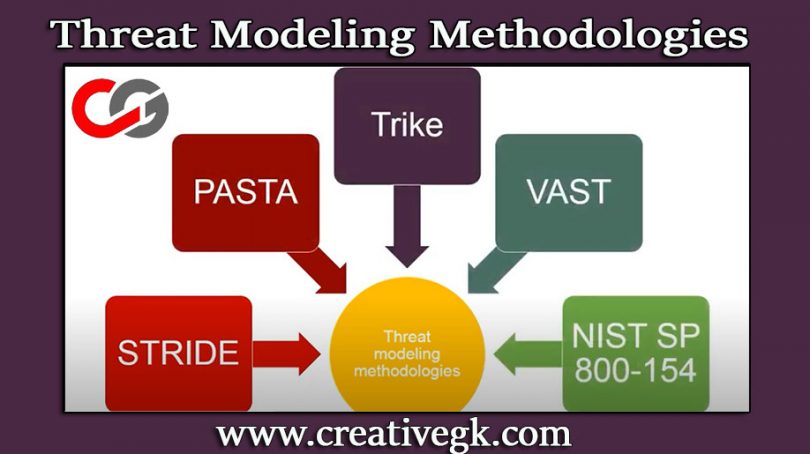
Just as there are various types of cyber-attacks, there are multiple methods to combat cybercrimes. Here are ten widely recognized threat modeling approaches commonly utilized today.
STRIDE:
STRIDE is a method created by Microsoft to help identify different types of security threats. It uses a simple way to remember the categories of threats:
Spoofing: When someone pretends to be another user or part of a system to deceive and gain access.
Tampering: Changing data in a system with harmful intentions.
Repudiation: The ability of an attacker to deny their malicious actions because there isn’t enough evidence.
Information Disclosure: Unauthorized access to protected information, revealing it to people who shouldn’t see it.
Denial of Service: When an attacker disrupts or overwhelms a system, making it unavailable to users.
Elevation of Privilege: Giving an attacker the ability to perform actions they shouldn’t be able to do.
DREAD:
DREAD is a method that was initially proposed for threat modeling but was later abandoned by Microsoft in 2008. However, it is still used by organizations like OpenStack to assess and prioritize security risks. It involves evaluating risks based on five categories:
Damage Potential: This category assesses the potential extent of damage that can occur if a weakness is exploited.
Reproducibility: It ranks the ease with which an attack can be replicated or reproduced.
Exploitability: It assigns a numerical rating to indicate the level of effort required to launch the attack.
Affected Users: This category represents the number of users who would be impacted if the exploit becomes widely available.
Discoverability: It measures how easily the threat can be discovered or identified.
By considering these categories, DREAD helps in ranking and evaluating security risks.
P.A.S.T.A:
P.A.S.T.A, which stands for Process for Attack Simulation and Threat Analysis, is a risk-centric methodology consisting of seven steps. It provides a systematic approach to identifying, enumerating and scoring threats. Experts analyze and create a detailed assessment of the identified threats. Analysis helps developers in designing a mitigation strategy that focuses on protecting specific assets within the application, using an attacker-centric perspective.
Trike:
Trike is a risk management approach that utilizes threat models as a tool. It involves creating threat models based on requirement models, which help to determine the level of risk considered “acceptable” for each asset class, as defined by stakeholders. Through an analysis of the requirement models, threats are identified and assigned risk values. These threat models are then used to construct a risk model, taking into account actions, assets, roles and calculated risk exposure. The completed risk model provides a comprehensive understanding of the potential risks associated with the system or project.
VAST:
VAST, stands for Visual, Agile and Simple Threat modeling, is a threat modeling approach that aims to provide practical and useful results tailored to the specific requirements of different stakeholders, including application architects, developers and cybersecurity personnel. It offers a distinct plan for visualizing both applications and infrastructure, making the creation and utilization of threat models accessible to individuals without specialized expertise in security. VAST emphasizes a user-friendly and agile process, enabling stakeholders to effectively address security concerns without extensive security knowledge.
Attack Tree:
An attack tree is like a map that shows different ways someone could try to attack something valuable. It has a main starting point; and then branches out with different steps or conditions that need to be met for each attack to work. Each step or condition only counts if the ones directly below it is also true. The tree also allows for different options or choices at each step, like taking different paths to reach the same goal.
Common Vulnerability Scoring System (CVSS):
The method is used to measure how serious a vulnerability is. It assigns a numerical score from 0 to 10, with 10 being the most severe. This score is then converted into categories like Low, Medium, High, or Critical, which helps organizations understand the level of risk. By using CVSS, organizations evaluate and prioritize their vulnerability management processes effectively.
T-MAP:
T-MAP is widely used in Commercial Off the Shelf (COTS) systems to determine the weights of attack paths. It uses UML class diagrams, which include information about access class, vulnerability, target assets and affected value. This approach helps in calculating the importance of different attack paths within the system.
OCTAVE:
It is a way to evaluate risks and plan for security in organizations.
It has three steps.
Understanding the threats to the organization.
Finding weaknesses in the organization’s information systems.
Creating a strategy to protect the organization’s important assets and making decisions about security.
Quantitative Threat Modeling Method:
The quantitative threat modeling method is a combination of attack trees, STRIDE and CVSS techniques. It helps address challenges in threat modeling for complex cyber-physical systems with interdependencies between components. The process involves creating attack trees for different attack categories and component attributes. Then, the CVSS method is used to calculate scores for each component in the tree.
It’s important to have various methods to assess security threats because the threats are real and hackers constantly come up with new ways to carry out their malicious activities.